Introduction

Read time: 10 minsInstall with Docker

Read time: 10 minsInstall on K8s

Read time: 10 minsInstall with Ansible

Read time: 10 minsInstall on Red Hat

Read time: 10 minsInstall on Ubuntu

Read time: 10 minsInstall on Amazon AWS

Read time: 10 minsInstall Tyk on Heroku

Read time: 10 minsInstall on Microsoft Azure
Tyk Dependencies and Database Support
MongoDB / PostgreSQL
Tyk Dashboard requires a persistent datastore for its operations. By default MongoDB is used. From Tyk v4.0, we also support PostgreSQL. See Database Options for a list of versions and drop-in replacements we support.Redis
Tyk Gateway requires Redis for its operations. Here is the list of supported versions: Supported Versions- Tyk 5.3 supports Redis 6.2.x, 7.0.x, and 7.2.x
- Tyk 5.2.x and earlier supports Redis 6.0.x and Redis 6.2.x only.
Tyk Gateway Architecture
The Tyk Gateway can run completely independently, requiring only a Redis database, and can scale horizontally: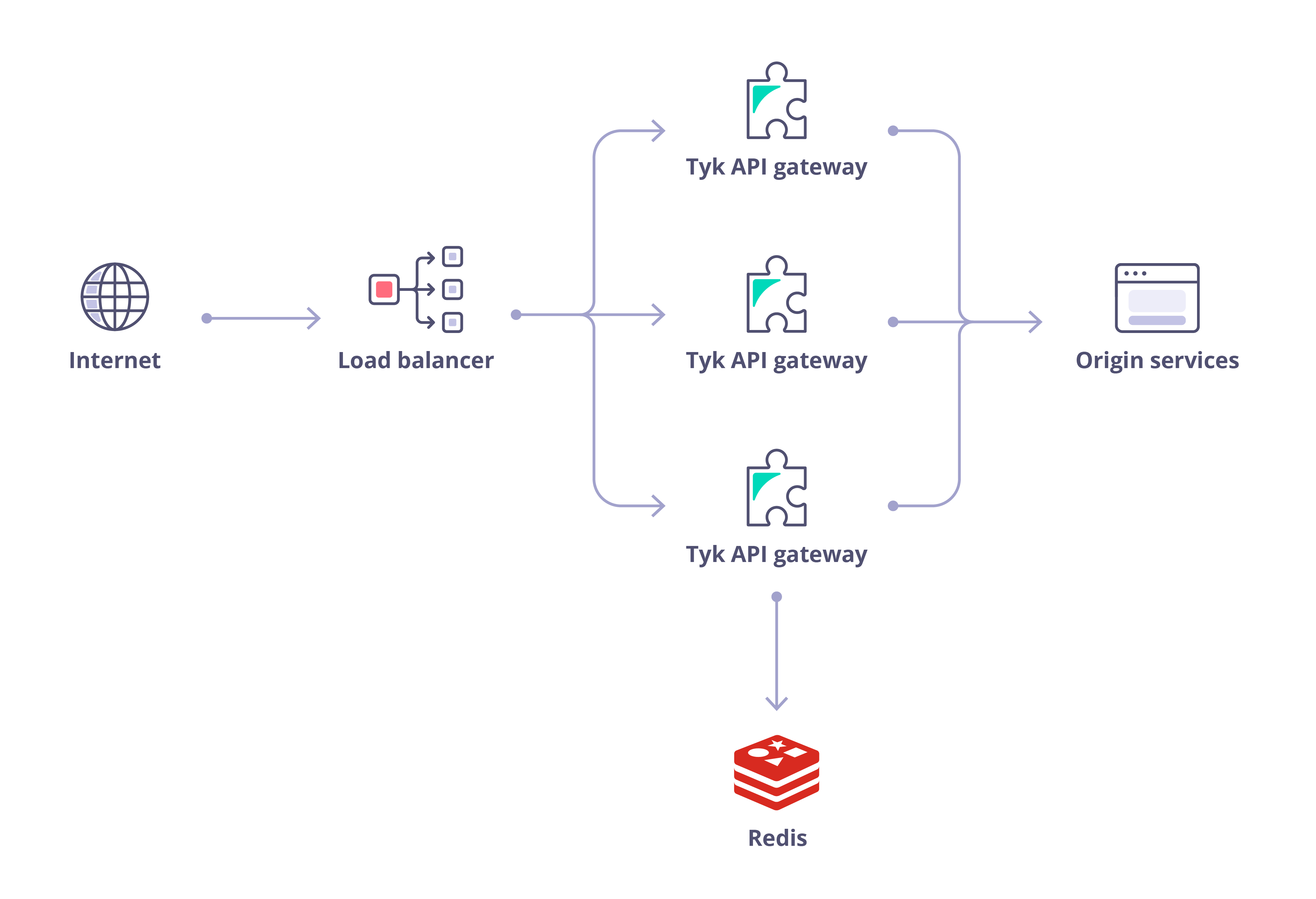
Init Systems
Tyk packages support SysVinit Linux init systems, systemd and Upstart (both 0.6.x and 1.x, [FYI - Ubuntu stopped supporting Upstart] upstart(https://askubuntu.com/questions/1024120/will-ubuntu-18-04-lts-still-support-upstart-or-do-we-have-to-change-to-systemd)). During package installation only one is chosen depending on the operating system support, e.g.:- CentOS 6, RHEL 6, Amazon Linux ship with Upstart 0.6.x
- Ubuntu 14.04, Debian Jessie with Upstart 1.x
- CentOS 7, RHEL 7, Ubuntu 16.04, Debian Stretch are running with systemd
- Certain older distros may only provide SysVinit but all of them typically provide compatibility with its scripts
install/inits directory inside the package directory.
This init system variance implies there are different ways to manage the services and collect service logs.
Upstart
For Upstart, service management can be performed through theinitctl or a set of start, stop, restart and status commands. Upstart 1.x also works with the service command.
systemd
For systemd, eithersystemctl or service commands may be utilized.
The service command can usually be used with SysVinit scripts, as well as invoking them directly.
- Upstart 0.6.x and SysVinit: log files are located in
/var/logsfor every respective service, e.g./var/logs/tyk-gateway.stderrand/var/logs/tyk-gateway.stdout - Upstart 1.x: by default everything is stored in
/var/logs/upstartdirectory, e.g./var/logs/upstart/tyk-gateway.log - systemd utilizes its own logging mechanism called journald, which is usable via the
journalctlcommand, e.g.journalctl -u tyk-gateway
Install on Kubernetes
The main way to install Tyk Self-Managed in a Kubernetes cluster is via Helm charts. We are actively working to add flexibility and more user flows to our chart. Please reach out to our teams on support or the cummunity forum if you have questions, requests or suggestions for improvements. Get started with one of our quick start guides: Or go to Tyk Stack helm chart for detailed installation instructions and configuration options.Install Tyk Stack with Helm Chart (PostgreSQL)
The following guides provide instructions to install Redis, PostgreSQL, and Tyk stack with default configurations. It is intended for quick start only. For production, you should install and configure Redis and PostgreSQL separately. Prerequisites Quick Start The following quick start guide explains how to use the Tyk Stack Helm chart to configure a Dashboard that includes:- Redis for key storage
- PostgreSQL for app config
- Tyk Pump to send analytics to PostgreSQL. It also opens a metrics endpoint where Prometheus (if available) can scrape from.
dashboard-svc-tyk-tyk-dashboard at port 3000. You can login to Dashboard using the admin email and password to start managing APIs. Tyk Gateway will be accessible through service gateway-svc-tyk-tyk-gateway.tyk.svc at port 8080.
1. Setup required credentials
First, you need to provide Tyk license, admin email and password, and API keys. We recommend to store them in secrets.
tyk-redis-master.tyk.svc:6379 (Tyk needs the name including the port)
The Bitnami chart also creates a secret tyk-redis which stores the connection password in redis-password. We will make use of this secret in installation later.
3. Install PostgreSQL (if you don’t already have PostgreSQL installed)
If you do not already have PostgreSQL installed, you may use these charts provided by Bitnami.
Ensure that you are installing PostgreSQL versions that are supported by Tyk. Please consult the list of supported versions that are compatible with Tyk.
dashboard-svc-tyk-tyk-dashboard at port 3000. You can login to Dashboard using the admin email and password to start managing APIs. Tyk Gateway will be accessible through service gateway-svc-tyk-tyk-gateway.tyk.svc at port 8080.
You are now ready to create an API.
For the complete installation guide and configuration options, please see Tyk Stack Helm Chart.
Install Tyk Stack with Helm Chart (MongoDB)
The following guides provide instructions to install Redis, MongoDB, and Tyk stack with default configurations. It is intended for quick start only. For production, you should install and configure Redis and MongoDB separately. Prerequisites- Kubernetes 1.19+
-
Helm 3+
If you want to enable Tyk Enterprise Developer Portal, please use PostgreSQL. MongoDB is not supported in Developer Portal.
- Redis for key storage
- MongoDB for app config
- Tyk Pump to send analytics to MongoDB. It also opens a metrics endpoint where Prometheus (if available) can scrape from.
dashboard-svc-tyk-tyk-dashboard at port 3000. You can login to Dashboard using the admin email and password to start managing APIs. Tyk Gateway will be accessible through service gateway-svc-tyk-tyk-gateway.tyk.svc at port 8080.
1. Setup required credentials
First, you need to provide Tyk license, admin email and password, and API keys. We recommend to store them in secrets.
tyk-redis-master.tyk.svc:6379 (Tyk needs the name including the port)
The Bitnami chart also creates a secret tyk-redis which stores the connection password in redis-password. We will make use of this secret in installation later.
Please make sure you are installing Redis versions that are supported by Tyk. Please refer to Tyk docs to get list of supported versions.
Please make sure you are installing MongoDB versions that are supported by Tyk. Please refer to Tyk docs to get list of supported versions.
Bitnami MongoDB image is not supported on darwin/arm64 architecture.
Ensure that you are installing MongoDB versions that are supported by Tyk. Please consult the list of supported versions that are compatible with Tyk.
dashboard-svc-tyk-tyk-dashboard at port 3000. You can login to Dashboard using the admin email and password to start managing APIs. Tyk Gateway will be accessible through service gateway-svc-tyk-tyk-gateway.tyk.svc at port 8080.
You are now ready to create an API.
For the complete installation guide and configuration options, please see Tyk Stack Helm Chart.
Install Tyk Stack on Windows with Helm
Installing Tyk on Kubernetes requires a multi-node Tyk license. If you are evaluating Tyk on Kubernetes, contact us to obtain an temporary license.
This deployment is NOT designed for production use or performance testing. The Tyk Pro Docker Demo is our full, Self-Managed solution, which includes our Gateway, Dashboard and analytics processing pipeline.This demo will run Tyk Self-Managed on your machine, which contains 5 containers: Tyk Gateway, Tyk Dashboard, Tyk Pump, Redis and either MongoDB or one of our supported SQL databases.This demo is great for proof of concept and demo purposes, but if you want to test performance, you need to move each component to a separate machine.
You use this at your own risk. Tyk is not supported on the Windows platform. However you can test it as a proof of concept using our Pro Demo Docker installation.
- MS Windows 10 Pro
- Tyk Helm Chart
- Docker Desktop for Windows running with a signed in Docker ID
- minikube
- Kubectl
- Helm
- Git for Windows
- Python for Windows
- PowerShell running as administrator
- Our Pro Demo Docker GitHub repo
- A free Tyk Self-Managed Developer license
- Microsoft Windows 10 Pro v1909 VM on Azure (Standard D2 v3 size)
- Docker Desktop for Windows 2.2.0.0 (Docker engine v19.03.5)
- helm v3.0.3
- minikube v1.7.1 (k8s v 1.17.2)
- kubectl v 1.17.0 (Note that kubectl is packaged with Docker Desktop for Windows, but the version may be incompatible with k8s)
Use Legacy Helm Chart
tyk-pro chart is deprecated. Please use our Tyk Stack helm chart instead.We recommend all users migrate to the tyk-stack Chart. Please review the Configuration section of the new helm chart and cross-check with your existing configurations while planning for migration.tyk-helm/tyk-pro will install full Tyk platform with Tyk Manager, Tyk Gateways and Tyk Pump into your Kubernetes cluster. You can also choose to enable the installation of Tyk Operator (to manage your APIs in a declarative way).
Prerequisites
- Tyk License If you are evaluating Tyk on Kubernetes, contact us to obtain a temporary license.
-
Data stores
The following are required for a Tyk Self-Managed installation:
- Redis - Should be installed in the cluster or reachable from inside the cluster (for SaaS option). You can find instructions for a simple Redis installation bellow.
- MongoDB or SQL - Should be installed in the cluster or be reachable by the Tyk Manager (for SaaS option).
- Helm Installed Helm 3 Tyk Helm Chart is using Helm v3 version (i.e. not Helm v2).
-
Add Tyk official Helm repo to your local Helm repository
-
Create namespace for your Tyk deployment
-
Getting the values.yaml of the chart
Before we proceed with installation of the chart you need to set some custom values.
To see what options are configurable on a chart and save that options to a custom values.yaml file run:
- Redis
- MongoDB
- SQL
Redis
Please make sure you are installing Redis versions that are supported by Tyk. Please refer to Tyk docs to get list of supported versions.
tyk-redis-master.tyk.svc.cluster.local:6379 (Tyk needs the name including the port)
You can update them in your local values.yaml file under redis.addrs and redis.pass
Alternatively, you can use --set flag to set it in Tyk installation. For example --set redis.pass=$REDIS_PASSWORDQuick Redis and MongoDB PoC installation
Another option for Redis and MongoDB, to get started quickly, is to use our simple-redis and simple-mongodb charts.
Please note that these provided charts must not ever be used in production and for anything
but a quick start evaluation only. Use external redis or Official Redis Helm chart in any other case.
We provide this chart, so you can quickly get up and running, however it is not meant for long term storage of data for example.
values.yaml file under dash.license field
or use --set dash.license={YOUR-LICENSE_KEY} with the helm install command.
Tyk Self-Managed licensing allow for different numbers of Gateway nodes to connect to a single Dashboard instance.
To ensure that your Gateway pods will not scale beyond your license allowance, please ensure that the Gateway’s resource kind is Deployment
and the replica count to your license node limit. By default, the chart is configured to work with a single node license: gateway.kind=Deployment and gateway.replicaCount=1.
Please NoteThere may be intermittent issues on the new pods during the rolling update process, when the total number of online
gateway pods is more than the license limit with lower amounts of Licensed nodes.
Important Note regarding MongoDBThe
--wait argument is important to successfully complete the bootstrap of your Tyk Manager.pump.enabled to true in values.yaml file.
Alternatively, you can use --set pump.enabled=true while doing helm install.
Quick Pump configuration(Supported from tyk helm v0.10.0)
1. Mongo Pump
To configure mongo pump, do following changings in values.yaml file:
- Set
backendtomongo. - Set connection string in
mongo.mongoURL.
values.yaml file:
- Set
backendtopostgres. - Set connection string parameters in
postgressection.
portal.bootstrap: false in your local values.yaml file.
Using TLS
You can turn on the TLS option under the gateway section in your local values.yaml file which will make your Gateway
listen on port 443 and load up a dummy certificate. You can set your own default certificate by replacing the file in the certs/ folder.
Mounting Files
To mount files to any of the Tyk stack components, add the following to the mounts array in the section of that component.
For example:
gateway.sharding.enabled option. Once you do that you
will also need to set the gateway.sharding.tags field with the tags that you want that particular Gateway to load. (ex. tags: “external,ingress”.)
You can then add those tags to your APIs in the API Designer, under the Advanced Options tab, and
the Segment Tags (Node Segmentation) section in your Tyk Dashboard.
Check Tyk Gateway Sharding for more details.
Install More Tyk Components
Installing Tyk Enterprise Developer Portal If you are deploying the Tyk Enterprise Developer Portal, set the appropriate values under theenterprisePortal section in your values.yaml. Please visit Tyk Enterprise Developer Portal installation for a step by step guide.
Note: Helm chart supports Enterprise Portal v1.2.0+Installing Tyk Self-managed Control Plane If you are deploying the Tyk Control plane, a.k.a MDCB, for a Tyk Multi Data Center Bridge deployment then you set the
mdcb.enabled: true option in the local values.yaml to add of the MDCB component to your installation.
Check Tyk Control plane for more configuration details.
This setting enables multi-cluster, multi Data-Center API management from a single dashboard.
Tyk Identity Broker (TIB)
The Tyk Identity Broker (TIB) is a micro-service portal that provides a bridge between various Identity Management Systems
such as LDAP, OpenID Connect providers and legacy Basic Authentication providers, to your Tyk installation.
See TIB for more details.
For SSO to Tyk Manager and Tyk developer portal purposes you do not need to install TIB, as its functionality is now
part of the Tyk Manager. However, if you want to run it separately (as you used to before this merge) or if you need it
as a broker for the Tyk Gateway you can do so.
Once you have installed your Tyk Gateway and Tyk Manager, you can configure TIB by adding its configuration environment variables
under the tib.extraEnvs section and updating the profile.json in your configs folder.
See our TIB GitHub repo.
Once you complete your modifications you can run the following command from the root of the repository to update your helm chart.
profiles.json definition in it. Please use tib.configMap.profiles value
to set the name of this ConfigMap (tyk-tib-profiles-conf by default).
Tyk Operator and Ingress
For a GitOps workflow used with a Tyk Self-Managed installation or setting the Tyk Gateway as a Kubernetes ingress controller, Tyk Operator enables you to manage API definitions, security policies and other Tyk features using Kubernetes manifest files.
To get started go to Tyk Operator.
Install on AWS Marketplace
Tyk offers a flexible and powerful API management solution through Tyk Cloud on the AWS Marketplace. Tyk Cloud is an end-to-end managed API platform where both the control plane and gateways are installed on AWS for a seamless, fully cloud-hosted experience. For those who need more deployment flexibility, Tyk Cloud also supports a Hybrid Gateway option. In this setup, the control plane remains hosted and managed by Tyk on AWS, while the gateways can be deployed on your preferred cloud provider or on-premises environment—allowing you to meet data locality and compliance needs without sacrificing control. Available AWS Deployment Regions You can deploy Tyk Cloud in the following AWS regions:- Singapore:
aws-ap-southeast-1 - Frankfurt, Germany:
aws-eu-central-1 - London, UK:
aws-eu-west-2 - N. Virginia, USA:
aws-us-east-1 - Oregon, USA:
aws-us-west-2 - Australia:
aws-ap-southeast-2
-
Spin up an EC2 instance, AWS Linux2 preferably, T2.Medium is fine
- add a public IP
- open up SG access to:
- 3000 for the Tyk Dashboard
- 8080 for the Tyk Gateway
- 22 TCP for SSH
-
SSH into the instance
ssh -i mykey.pem ec2-user@public-ec2-ip - Install Git, Docker, & Docker Compose Feel free to copy paste these
- Clone the Tyk Pro Docker repo
- Add the license key to
confs/tyk_analytics.confinto thelicense_key variableusing “vi” or “nano”, etc
tyk_analytics.conf, license_key should look something like this, with a real license however:
"license_key": "eyJhbGciOiJSUzI1NiIsInR5cCI...WQ",
- Run the containers via
docker-compose
- Visit
- Add the following to
confs/tyk.conf
- Add the following to
confs/tyk_analytics.conf
- Generate self-signed Certs: (Or bring your own CA signed)
- Mount your certs to containers through
docker-compose.yml
- Restart your containers with the mounted files
- Download the bootstrap script onto EC2 machine
- Apply execute permissions to file:
chmod +x bootstrap.sh
- Run the bootstrap script
./bootstrap.sh localhost
- Done! use the generated user and password to log into The Tyk Dashboard
Install with Ansible
RequirementsAnsible is required to run the following commands.
-
clone the tyk-ansible repositry
-
cdinto the directory -
Run initialisation script to initialise environment
-
Modify
hosts.ymlfile to update ssh variables to your server(s). You can learn more about the hosts file here -
Run ansible-playbook to install the following:
- Redis
- MongoDB or PostgreSQL
- Tyk Dashboard
- Tyk Gateway
- Tyk Pump
You can choose to not install Redis, MongoDB or PostgreSQL by removing the-t redisor-t mongodbor-t pgsqlHowever Redis and MongoDB or PostgreSQL are a requirement and need to be installed for the Tyk Pro installation to run.For a production environment, we recommend that the Gateway, Dashboard and Pump are installed on separate machines. If installing multiple Gateways, you should install each on a separate machine. See Planning for Production For more details.
| Distribution | Version | Supported |
|---|---|---|
| Amazon Linux | 2 | ✅ |
| CentOS | 8 | ✅ |
| CentOS | 7 | ✅ |
| Debian | 10 | ✅ |
| Debian | 9 | ✅ |
| RHEL | 8 | ✅ |
| RHEL | 7 | ✅ |
| Ubuntu | 21 | ✅ |
| Ubuntu | 20 | ✅ |
| Ubuntu | 18 | ✅ |
| Ubuntu | 16 | ✅ |
vars/tyk.yaml
| Variable | Default | Comments |
|---|---|---|
| secrets.APISecret | 352d20ee67be67f6340b4c0605b044b7 | API secret |
| secrets.AdminSecret | 12345 | Admin secret |
| redis.host | Redis server host if different than the hosts url | |
| redis.port | 6379 | Redis server listening port |
| redis.pass | Redis server password | |
| redis.enableCluster | false | Enable if redis is running in cluster mode |
| redis.storage.database | 0 | Redis server database |
| redis.tls | false | Enable if redis connection is secured with SSL |
| mongo.host | MongoDB server host if different than the hosts url | |
| mongo.port | 27017 | MongoDB server listening port |
| mongo.tls | false | Enable if mongo connection is secured with SSL |
| pgsql.host | PGSQL server host if different than the hosts url | |
| pgsql.port | 5432 | PGSQL server listening port |
| pgsql.tls | false | Enable if pgsql connection is secured with SSL |
| dash.license | Dashboard license | |
| dash.service.host | Dashboard server host if different than the hosts url | |
| dash.service.port | 3000 | Dashboard server listening port |
| dash.service.proto | http | Dashboard server protocol |
| dash.service.tls | false | Set to true to enable SSL connections |
| gateway.service.host | Gateway server host if different than the hosts url | |
| gateway.service.port | 8080 | Gateway server listening port |
| gateway.service.proto | http | Gateway server protocol |
| gateway.service.tls | false | Set to true to enable SSL connections |
| gateway.sharding.enabled | false | Set to true to enable filtering (sharding) of APIs |
| gateway.sharding.tags | The tags to use when filtering (sharding) Tyk Gateway nodes. Tags are processed as OR operations. If you include a non-filter tag (e.g. an identifier such as node-id-1, this will become available to your Dashboard analytics) | |
| gateway.rpc.connString | Use this setting to add the URL for your MDCB or load balancer host | |
| gateway.rpc.useSSL | true | Set this option to true to use an SSL RPC connection |
| gateway.rpc.sslInsecureSkipVerify | true | Set this option to true to allow the certificate validation (certificate chain and hostname) to be skipped. This can be useful if you use a self-signed certificate |
| gateway.rpc.rpcKey | Your organization ID to connect to the MDCB installation | |
| gateway.rpc.apiKey | This the API key of a user used to authenticate and authorize the Gateway’s access through MDCB. The user should be a standard Dashboard user with minimal privileges so as to reduce any risk if the user is compromised. The suggested security settings are read for Real-time notifications and the remaining options set to deny | |
| gateway.rpc.groupId | This is the zone that this instance inhabits, e.g. the cluster/data-center the Gateway lives in. The group ID must be the same across all the Gateways of a data-center/cluster which are also sharing the same Redis instance. This ID should also be unique per cluster (otherwise another Gateway cluster can pick up your keyspace events and your cluster will get zero updates). |
vars/redis.yaml
| Variable | Default | Comments |
|---|---|---|
| redis_bind_interface | 0.0.0.0 | Binding address of Redis |
vars/mongodb.yaml
| Variable | Default | Comments |
|---|---|---|
| bind_ip | 0.0.0.0 | Binding address of MongoDB |
| mongodb_version | 4.4 | MongoDB version |
vars/pgsql.yaml
| Variable | Default | Comments |
|---|---|---|
| postgresql_databases[] | [] | Array of DBs to be created |
| postgresql_databases[].name | tyk_analytics | Database name |
| postgresql_users[] | [] | Array of users to be created |
postgresql_users[0].name | default | User name |
postgresql_users[0].password | topsecretpassword | User password |
| postgresql_global_config_options[] | [] | Postgres service config options |
postgresql_global_config_options[1].option | listen_addresses | Listen address binding for the service |
postgresql_global_config_options[1].value | * | Default value to listen to all addresses |
| postgresql_hba_entries[] | [] | Host based authenticaiton list |
postgresql_hba_entries[4].type | host | Entry type |
postgresql_hba_entries[4].database | tyk_analytics | Which database this entry will give access to |
postgresql_hba_entries[4].user | default | What users this gain access from this entry |
postgresql_hba_entries[4].address | 0.0.0.0/0 | What addresses this gain access from this entry |
postgresql_hba_entries[4].auth_method | md5 | What authentication method to to use for the users |
Install using Bootstrap CLI
To list the available flags, executetyk-analytics bootstrap -h:
bootstrap command makes bootstrapping easier. It helps you to create organizations and users. The command needs a
config file path. By default, it looks at tyk_analytics.conf in the directory where the tyk-analytics binary is located.
For example:
tyk-analytics bootstrap
You can also give the path of a custom config file with the --conf flag. For example:
tyk-analytics bootstrap --conf some-directory/custom.conf
The tool can work in both auto and interactive modes. You can use the flags while running the command or you can just run
it without flags and use interactive mode.
Environment Variables
You can override the config values by environment variables. See how to configure an environment variable.
For example, you can override hostname, port, mongo url, redis host and redis port values by exporting the following variables:
- TYK_DB_HOSTCONFIG_HOSTNAME
- TYK_DB_LISTENPORT
- TYK_DB_MONGOURL
- TYK_DB_REDISHOST
- TYK_DB_REDISPORT
Install with Docker
Tyk has three containers that are available to set up a Docker installation: All three are required for a full deployment. We recommend that each container is installed on a separate machine for optimum performance. From v5.5.0 onwards, these images are based on distroless. This means that you will not be able to obtain a shell withdocker run --rm -it tykio/tyk-gateway:v5.5.0 sh. The image can be inspected with tools like dive or Docker Desktop.
We also have a Docker Tyk Pro Demo, which installs our full Self-Managed solution, which includes our Gateway, Dashboard, and analytics processing pipeline. This demo will run Tyk Self-Managed on your machine.
Install on Heroku
Install Tyk API Gateway on Heroku A full Tyk Self-Managed installation can be deployed to Heroku dynos and workers using Heroku Container Registry and Runtime functionality. This guide will utilize Tyk Docker images with a small amount of customization as well as an external MongoDB service. Prerequisites- Docker daemon installed and running locally
- Heroku account, the free plan is sufficient for a basic PoC but not recommended for production usage
- Heroku CLI installed
- MongoDB service (such as Atlas, mLab, or your own deployment), this guide is based on MongoDB Atlas but others should work as well
- Tyk License (note that in case of running multiple gateway dynos, license type must match)
- Checkout the Tyk quickstart repository from GitHub
- Python 2 or 3 in order to execute the bootstrap script
--space flag must be added to the command if the app is being created in a private space, see more details in the section on Heroku private spaces (below).hobby-dev plan for demonstration purposes but that’s not suitable for production), replacing the app name with your own:
heroku config command and check for the Redis endpoint:
Dockerfile.web for the web dyno, a config file for the Dashboard, entrypoint script for the Docker container and a bootstrap script for seeding the dashboard instance with sample data. All these files are editable for your purposes but have sane defaults for a PoC.
You can use the
FROM statement in Dockerfile.web to use specific dashboard version and upgrade when needed instead of relying on the latest tag.tyk_analytics.conf file or injecting them as environment variables via heroku config. In this guide we’ll use the latter for simplicity of demonstration but there is merit to both methods.
First let’s set the license key:
pump.conf file):
analytics directory of the quickstart repo:
dashboard/bootstrap.sh script:
tyk.conf or injected with heroku config.
To get things going we’ll need to set following options for the Dashboard endpoint (substituting the actual endpoint and the app name, now for the gateway app):
heroku logs -a infinite-plains-14949) to check that deployment was successful, also the node should be registered by the Dashboard in “System Management” -> “Nodes and Licenses” section.
You’re ready to follow the guide on creating and managing your APIs with this Heroku deployment.
To use the geographic log distribution feature in the Dashboard please supply the GeoLite2 DB in the
gateway directory, uncomment the marked line in Dockerfile.web and set the analytics_config.enable_geo_ip setting (or TYK_GW_ANALYTICSCONFIG_ENABLEGEOIP env var) to true.--space flag, e.g.:
private-7. Please refer to Heroku’s Redis with private spaces guide for more information.
Apps in private spaces don’t enable SSL/TLS by default. It needs to be configured in the app settings along with the domain name for it. If it’s not enabled, please make sure that configs that refer to corresponding hosts are using HTTP instead of HTTPS and related ports (80 for HTTP).
Gateway Plugins
In order to enable rich plugins for the Gateway, please set the following Heroku config option to either python or lua depending on the type of plugins used:
Dockerfile and replacing the base image version tag. E.g. changing FROM tykio/tyk-gateway:v2.5.4 to FROM tykio/tyk-gateway:v2.6.1 will pull the Tyk gateway 2.6.1. We highly recommend specifying concrete version tags instead of latest for better house keeping.
Once these changes have been made just run heroku container:push --recursive -a app_name on the corresponding directory as shown previously in this guide. This will do all the building and pushing as well as gracefully deploying on your Heroku app.
Please refer to Heroku documentation on containers and registry for more information.
Install on Microsoft Azure
Azure is Microsoft’s cloud services platform. It supports both the running of Ubuntu Servers, as well as Docker and Docker-Compose. For more details, see the Azure Documentation. **Tyk Installation Options for Azure ** Azure allows you to install Tyk in the following ways: On-Premises- Via our Ubuntu Setup on an installed Ubuntu Server on Azure.
- Via our Docker Installation using Azure’s Docker support.
We also have a blog post that walks you through installing Tyk on Azure.
Install to Google Cloud
GCP is Google’s Cloud services platform. It supports both the running of Ubuntu Servers and Docker. For more details, see the Google Cloud Documentation. **Tyk Installation Options for Google CLoud ** Google Cloud allows you to install Tyk in the following ways: On-Premises- Via our Ubuntu Setup on an installed Ubuntu Server within Google Cloud.
- Via our Docker Installation using Google Cloud’s Docker support.
- Configure Cloud Run to have the CPU always allocated option enabled. Otherwise, the Tyk Pump container needs to warm up, which takes approximately 1 min. Subsequently, by this time the stats are removed from Redis.
- Update the Tyk Gateway configuration to keep the stats for 3 mins to allow Tyk Pump to process them. This value should be greater than the Pump purge delay to ensure the analytics data exists long enough in Redis to be processed by the Pump.
Install Tyk on Red Hat (RHEL / CentOS)
Select the preferred way of installing Tyk by selecting Shell or Ansible tab for instructions. There are 4 components which needs to be installed. Each can be installed via shell or ansibleInstall Database
Using Shell
Supported Distributions| Distribution | Version | Supported |
|---|---|---|
| CentOS | 7 | ✅ |
| RHEL | 9 | ✅ |
| RHEL | 8 | ✅ |
| RHEL | 7 | ✅ |
Redis Tyk Gateway has a dependency on Redis. Follow the steps provided by Red Hat to make the installation of Redis, conducting a search for the correct version and distribution. Storage Database Tyk Dashboard has a dependency on a storage database that can be PostgreSQL or MongoDB. Option 1: Install PostgreSQL Check the PostgreSQL supported versions. Follow the steps provided by PostgreSQL to install it. Configure PostgreSQL Create a new role/user
Check the MongoDB supported versions. Follow the steps provided by MongoDB to install it. Optionally initialize the database and enable automatic start:
Using Ansible
You can install Tyk on RHEL or CentOS using our YUM repositories. Follow the guides and tutorials in this section to have Tyk up and running in no time. The order is to install Tyk Dashboard, then Tyk Pump and then Tyk Gateway for a full stack.- Dashboard
- Pump
-
Gateway
For a production environment, we recommend that the Tyk Gateway, Tyk Dashboard and Tyk Pump are installed on separate machines. If installing multiple Tyk Gateways, you should install each on a separate machine. See Planning for Production for more details.
| Distribution | Version | Supported |
|---|---|---|
| CentOS | 7 | ✅ |
| RHEL | 8 | ✅ |
| RHEL | 7 | ✅ |
-
clone the tyk-ansible repositry
-
cdinto the directory
-
Run initialisation script to initialise environment
-
Modify
hosts.ymlfile to update ssh variables to your server(s). You can learn more about the hosts file here -
Run ansible-playbook to install the following:
- Redis
- MongoDB or PostgreSQL
- Tyk Dashboard
- Tyk Gateway
- Tyk Pump
You can choose to not install Redis, MongoDB or PostgreSQL by removing the-t redisor-t mongodbor-t pgsqlHowever Redis and MongoDB or PostgreSQL are a requirement and need to be installed for the Tyk Pro installation to run.
vars/tyk.yaml
| Variable | Default | Comments |
|---|---|---|
| secrets.APISecret | 352d20ee67be67f6340b4c0605b044b7 | API secret |
| secrets.AdminSecret | 12345 | Admin secret |
| redis.host | Redis server host if different than the hosts url | |
| redis.port | 6379 | Redis server listening port |
| redis.pass | Redis server password | |
| redis.enableCluster | false | Enable if redis is running in cluster mode |
| redis.storage.database | 0 | Redis server database |
| redis.tls | false | Enable if redis connection is secured with SSL |
| mongo.host | MongoDB server host if different than the hosts url | |
| mongo.port | 27017 | MongoDB server listening port |
| mongo.tls | false | Enable if mongo connection is secured with SSL |
| pgsql.host | PGSQL server host if different than the hosts url | |
| pgsql.port | 5432 | PGSQL server listening port |
| pgsql.tls | false | Enable if pgsql connection is secured with SSL |
| dash.license | Dashboard license | |
| dash.service.host | Dashboard server host if different than the hosts url | |
| dash.service.port | 3000 | Dashboard server listening port |
| dash.service.proto | http | Dashboard server protocol |
| dash.service.tls | false | Set to true to enable SSL connections |
| gateway.service.host | Gateway server host if different than the hosts url | |
| gateway.service.port | 8080 | Gateway server listening port |
| gateway.service.proto | http | Gateway server protocol |
| gateway.service.tls | false | Set to true to enable SSL connections |
| gateway.sharding.enabled | false | Set to true to enable filtering (sharding) of APIs |
| gateway.sharding.tags | The tags to use when filtering (sharding) Tyk Gateway nodes. Tags are processed as OR operations. If you include a non-filter tag (e.g. an identifier such as node-id-1, this will become available to your Dashboard analytics) | |
| gateway.rpc.connString | Use this setting to add the URL for your MDCB or load balancer host | |
| gateway.rpc.useSSL | true | Set this option to true to use an SSL RPC connection |
| gateway.rpc.sslInsecureSkipVerify | true | Set this option to true to allow the certificate validation (certificate chain and hostname) to be skipped. This can be useful if you use a self-signed certificate |
| gateway.rpc.rpcKey | Your organization ID to connect to the MDCB installation | |
| gateway.rpc.apiKey | This the API key of a user used to authenticate and authorize the Gateway’s access through MDCB. The user should be a standard Dashboard user with minimal privileges so as to reduce any risk if the user is compromised. The suggested security settings are read for Real-time notifications and the remaining options set to deny | |
| gateway.rpc.groupId | This is the zone that this instance inhabits, e.g. the cluster/data-center the Gateway lives in. The group ID must be the same across all the Gateways of a data-center/cluster which are also sharing the same Redis instance. This ID should also be unique per cluster (otherwise another Gateway cluster can pick up your keyspace events and your cluster will get zero updates). |
vars/redis.yaml
| Variable | Default | Comments |
|---|---|---|
| redis_bind_interface | 0.0.0.0 | Binding address of Redis |
vars/mongodb.yaml
| Variable | Default | Comments |
|---|---|---|
| bind_ip | 0.0.0.0 | Binding address of MongoDB |
| mongodb_version | 4.4 | MongoDB version |
vars/pgsql.yaml
| Variable | Default | Comments |
|---|---|---|
| postgresql_databases[] | [] | Array of DBs to be created |
| postgresql_databases[].name | tyk_analytics | Database name |
| postgresql_users[] | [] | Array of users to be created |
postgresql_users[0].name | default | User name |
postgresql_users[0].password | topsecretpassword | User password |
| postgresql_global_config_options[] | [] | Postgres service config options |
postgresql_global_config_options[1].option | listen_addresses | Listen address binding for the service |
postgresql_global_config_options[1].value | * | Default value to listen to all addresses |
| postgresql_hba_entries[] | [] | Host based authenticaiton list |
postgresql_hba_entries[4].type | host | Entry type |
postgresql_hba_entries[4].database | tyk_analytics | Which database this entry will give access to |
postgresql_hba_entries[4].user | default | What users this gain access from this entry |
postgresql_hba_entries[4].address | 0.0.0.0/0 | What addresses this gain access from this entry |
postgresql_hba_entries[4].auth_method | md5 | What authentication method to to use for the users |
Install Dashboard
Using Shell
Tyk has its own signed RPMs in a YUM repository hosted by the kind folks at packagecloud.io, which makes it easy, safe and secure to install a trusted distribution of the Tyk Gateway stack. This configuration should also work (with some tweaks) for CentOS. Prerequisites- Ensure port
3000is open: This is used by the Dashboard to provide the GUI and the Classic Developer Portal. - Follow the steps provided in this link Getting started on Red Hat (RHEL / CentOS) to install and configure Tyk dependencies.
-
Set up YUM Repositories
First, install two package management utilities
yum-utilsand a file downloading toolwget:Then install Python: -
Configure and Install the Tyk Dashboard
Create a file named
/etc/yum.repos.d/tyk_tyk-dashboard.repothat contains the repository configuration settings for YUM repositoriestyk_tyk-dashboardandtyk_tyk-dashboard-sourceused to download packages from the specified URLs, including GPG key verification and SSL settings, on a Linux system. Make sure to replaceeland8in the config below with your Linux distribution and version:We’ll need to update the YUM package manager’s local cache, enabling only thetyk_tyk-dashboardrepository while disabling all other repositories--disablerepo='*' --enablerepo='tyk_tyk-dashboard', and confirm all prompts-y.Install Tyk dashboard: -
Confirm Redis and MongoDB or PostgreSQL are running
Start Redis since it is always required by the Dashboard.
Then start either MongoDB or PostgreSQL depending on which one you are using.
- Configure Tyk Dashboard
- MongoDB
- SQL
<Redis Hostname>, <Mongo IP Address> and <Mongo Port> with your own values to run this script.--listenport=3000: Tyk Dashboard (and Portal) to listen on port3000.--redishost=<hostname>: Tyk Dashboard should use the local Redis instance.--redisport=6379: The Tyk Dashboard should use the default port.--domain="XXX.XXX.XXX.XXX": Bind the Dashboard to the IP or DNS hostname of this instance (required).--mongo=mongodb://<Mongo IP Address>:<Mongo Port>/tyk_analytics: Use the local MongoDB (should always be the same as the Gateway).--storage=postgres: In case, your preferred storage Database is PostgreSQL, use storage type “postgres” and specify connection string.--connection_string=postgresql://<User>:<Password>@<PostgreSQL Host Name>:<PostgreSQL Port>/<PostgreSQL DB>: Use the PostgreSQL instance provided in the connection string (should always be the same as the gateway).--tyk_api_hostname=$HOSTNAME: The Tyk Dashboard has no idea what hostname has been given to Tyk, so we need to tell it, in this instance we are just using the local HOSTNAME env variable, but you could set this to the public-hostname/IP of the instance.--tyk_node_hostname=http://localhost: The Tyk Dashboard needs to see a Tyk node in order to create new tokens, so we need to tell it where we can find one, in this case, use the one installed locally.--tyk_node_port=8080: Tell the Dashboard that the Tyk node it should communicate with is on port 8080.--portal_root=/portal: We want the Portal to be shown on /portal of whichever domain we set for the Portal.
-
Start Tyk Dashboard
Notice how we haven’t actually started the gateway yet, because this is a Dashboard install, we need to enter a license first.To check the logs from the deployment run:
When using PostgreSQL you may receive the error:
"failed SASL auth (FATAL: password authentication failed for user...)", follow these steps to address the issue:- Open the terminal or command prompt on your PostgreSQL server.
- Navigate to the location of the
pg_hba.conffile. This file is typically located at/var/lib/pgsql/13/data/pg_hba.conf. - Open the
pg_hba.conffile using a text manipulation tool. - In the
pg_hba.conffile, locate the entry corresponding to the user encountering the authentication error. This entry might resemble the following:
- In the entry, find the METHOD column. It currently has the value scram-sha-256.
- Replace scram-sha-256 with md5, so the modified entry looks like this:
- Save the changes you made to the
pg_hba.conffile. - Restart the PostgreSQL service to apply the modifications:
-
Enter Dashboard license
Add your license in
/var/opt/tyk-dashboard/tyk_analytics.confin thelicensefield. If all is going well, you will be taken to a Dashboard setup screen - we’ll get to that soon. -
Restart the Dashboard process
Because we’ve just entered a license via the UI, we need to make sure that these changes get picked up, so to make sure things run smoothly, we restart the Dashboard process (you only need to do this once) and (if you have it installed) then start the gateway:
-
Go to the Tyk Dashboard URL
Go to the following URL to access to the Tyk Dashboard:
You should get to the Tyk Dashboard Setup screen:
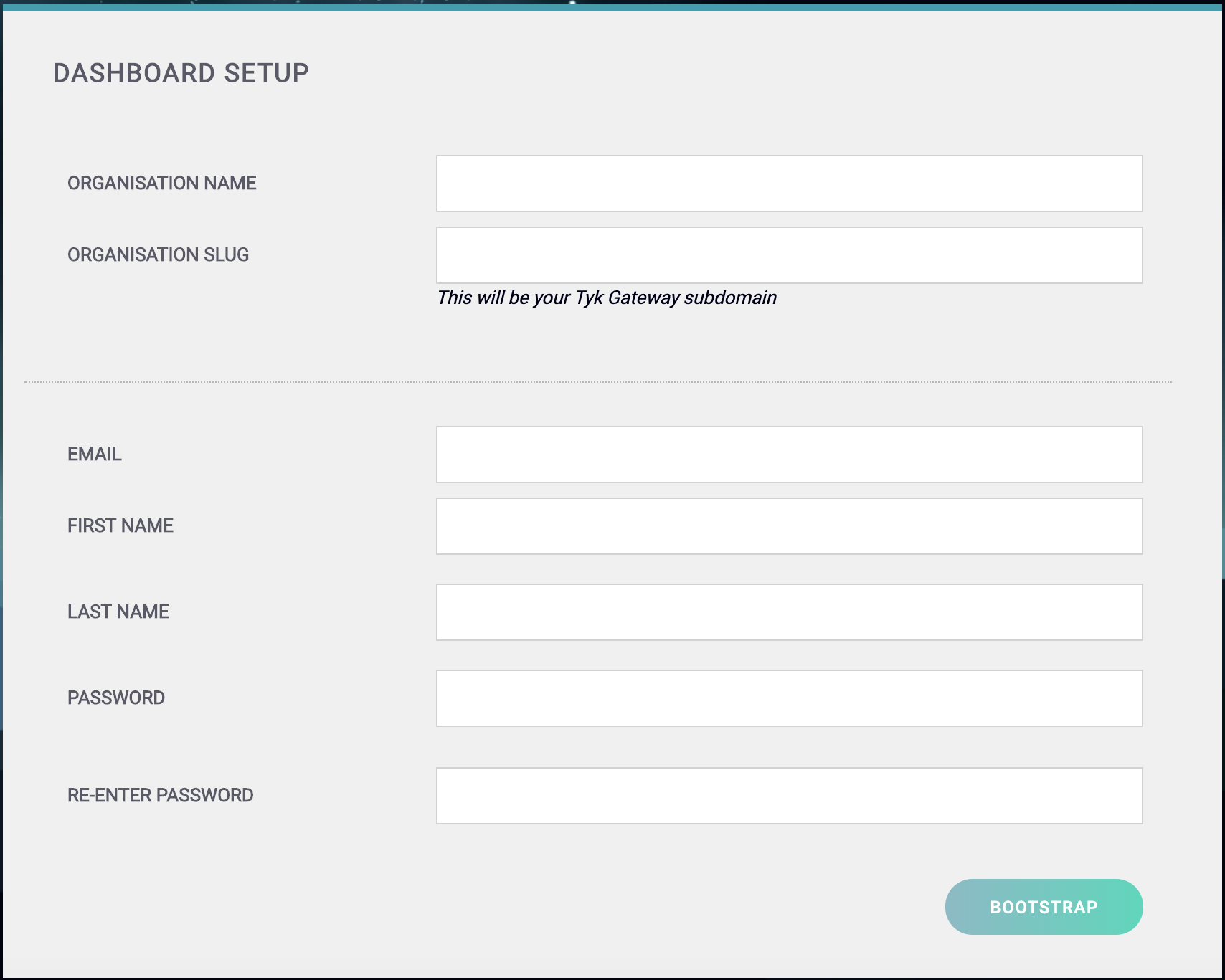
-
Create your Organization and Default User
You need to enter the following:
- Your Organization Name
- Your Organization Slug
- Your User Email Address
- Your User First and Last Name
- A Password for your User
- Re-enter your user Password
Click Bootstrap to save the details.For a password, we recommend a combination of alphanumeric characters, with both upper and lower case letters. -
Login to the Dashboard
You can now log in to the Tyk Dashboard from
127.0.0.1:3000, using the username and password created in the Dashboard Setup screen. Configure your Developer Portal To set up your Developer Portal follow our Self-Managed tutorial on publishing an API to the Portal Catalog.
Using Ansible
Getting Started- clone the tyk-ansible repository
cdinto the directory
- Run initialisation script to initialise environment
-
Modify
hosts.ymlfile to update ssh variables to your server(s). You can learn more about the hosts file here -
Run ansible-playbook to install
tyk-dashboard
| Distribution | Version | Supported |
|---|---|---|
| Amazon Linux | 2 | ✅ |
| CentOS | 8 | ✅ |
| CentOS | 7 | ✅ |
| RHEL | 8 | ✅ |
| RHEL | 7 | ✅ |
vars/tyk.yaml
| Variable | Default | Comments |
|---|---|---|
| secrets.APISecret | 352d20ee67be67f6340b4c0605b044b7 | API secret |
| secrets.AdminSecret | 12345 | Admin secret |
| dash.license | Dashboard license | |
| dash.service.host | Dashboard server host if different than the hosts url | |
| dash.service.port | 3000 | Dashboard server listening port |
| dash.service.proto | http | Dashboard server protocol |
| dash.service.tls | false | Set to true to enable SSL connections |
Install Pump
Using Shell
Tyk has it’s own signed RPMs in a YUM repository hosted by the kind folks at packagecloud.io, which makes it easy, safe and secure to install a trusted distribution of the Tyk Gateway stack. This tutorial will run on an Amazon AWS Red Hat Enterprise Linux 7.1 instance. We will install Tyk Pump with all dependencies stored locally. We’re installing on at2.micro because this is a tutorial, you’ll need more RAM and more cores for better performance.
This configuration should also work (with some tweaks) for CentOS.
Prerequisites
We are assuming that Redis and either MongoDB or SQL are installed (these are installed as part of the Tyk Gateway and Dashboard installation guides)
Step 1: Set up YUM Repositories
First, we need to install some software that allows us to use signed packages:
/etc/yum.repos.d/tyk_tyk-pump.repo that contains the repository configuration below:
Make sure to replace el and 7 in the config below with your Linux distribution and version:
Step 3: Configure Tyk Pump If you don’t complete this step, you won’t see any analytics in your Dashboard, so to enable the analytics service, we need to ensure Tyk Pump is running and configured properly. Configure Tyk Pump for MongoDB
You need to replace
<hostname> for --redishost=<hostname>, and <Mongo IP Address>, <Mongo Port> for --mongo=mongodb://<Mongo IP Address>:<Mongo Port>/ with your own values to run this script.You need to replace
<hostname> for --redishost=<hostname>, and <Postgres Host Name>,<Port>, <User>, <Password>, <DB> for --postgres="host=<Postgres Host Name> port=<Port> user=<User> password=<Password> dbname=<DB>" with your own values to run this script.Using Ansible
Getting Started- clone the tyk-ansible repositry
cdinto the directory
- Run initialisation script to initialise environment
-
Modify
hosts.ymlfile to update ssh variables to your server(s). You can learn more about the hosts file here -
Run ansible-playbook to install
tyk-pump
| Distribution | Version | Supported |
|---|---|---|
| Amazon Linux | 2 | ✅ |
| CentOS | 8 | ✅ |
| CentOS | 7 | ✅ |
| RHEL | 8 | ✅ |
| RHEL | 7 | ✅ |
Install Gateway
Using Shell
Tyk has it’s own signed RPMs in a YUM repository hosted by the kind folks at packagecloud.io, which makes it easy, safe and secure to install a trusted distribution of the Tyk Gateway stack. This tutorial will run on an Amazon AWS Red Hat Enterprise Linux 7.1 instance. We will install Tyk Gateway with all dependencies stored locally. We’re installing on at2.micro because this is a tutorial, you’ll need more RAM and more cores for better performance.
This configuration should also work (with some tweaks) for CentOS.
Prerequisites
- Ensure port
8080is open: this is used in this guide for Gateway traffic (API traffic to be proxied) - EPEL (Extra Packages for Enterprise Linux) is a free, community based repository project from Fedora which provides high quality add-on software packages for Linux distribution including RHEL, CentOS, and Scientific Linux. EPEL isn’t a part of RHEL/CentOS but it is designed for major Linux distributions. In our case we need it for Redis. Install EPEL using the instructions here.
/etc/yum.repos.d/tyk_tyk-gateway.repo that contains the repository configuration below https://packagecloud.io/tyk/tyk-gateway/install#manual-rpm:
Using Ansible
Requirements Ansible - required for running the commands below. Use the Shell tab for instructions to install Tyk from a shell. Getting Started- clone the tyk-ansible repositry
cdinto the directory
- Run initialisation script to initialise environment
-
Modify
hosts.ymlfile to update ssh variables to your server(s). You can learn more about the hosts file here -
Run ansible-playbook to install
tyk-gateway
| Distribution | Version | Supported |
|---|---|---|
| Amazon Linux | 2 | ✅ |
| CentOS | 8 | ✅ |
| CentOS | 7 | ✅ |
| RHEL | 8 | ✅ |
| RHEL | 7 | ✅ |
vars/tyk.yaml
| Variable | Default | Comments |
|---|---|---|
| secrets.APISecret | 352d20ee67be67f6340b4c0605b044b7 | API secret |
| secrets.AdminSecret | 12345 | Admin secret |
| gateway.service.host | Gateway server host if different than the hosts url | |
| gateway.service.port | 8080 | Gateway server listening port |
| gateway.service.proto | http | Gateway server protocol |
| gateway.service.tls | false | Set to true to enable SSL connections |
| gateway.sharding.enabled | false | Set to true to enable filtering (sharding) of APIs |
| gateway.sharding.tags | The tags to use when filtering (sharding) Tyk Gateway nodes. Tags are processed as OR operations. If you include a non-filter tag (e.g. an identifier such as node-id-1, this will become available to your Dashboard analytics) | |
| gateway.rpc.connString | Use this setting to add the URL for your MDCB or load balancer host | |
| gateway.rpc.useSSL | true | Set this option to true to use an SSL RPC connection |
| gateway.rpc.sslInsecureSkipVerify | true | Set this option to true to allow the certificate validation (certificate chain and hostname) to be skipped. This can be useful if you use a self-signed certificate |
| gateway.rpc.rpcKey | Your organization ID to connect to the MDCB installation | |
| gateway.rpc.apiKey | This the API key of a user used to authenticate and authorize the Gateway’s access through MDCB. The user should be a standard Dashboard user with minimal privileges so as to reduce any risk if the user is compromised. The suggested security settings are read for Real-time notifications and the remaining options set to deny | |
| gateway.rpc.groupId | This is the zone that this instance inhabits, e.g. the cluster/data-center the Gateway lives in. The group ID must be the same across all the Gateways of a data-center/cluster which are also sharing the same Redis instance. This ID should also be unique per cluster (otherwise another Gateway cluster can pick up your keyspace events and your cluster will get zero updates). |
Configure Tyk Gateway with the Dashboard
Prerequisites This configuration assumes that you have already installed Tyk Dashboard, and have decided on the domain names for your Dashboard and your Portal. They must be different. For testing purposes, it is easiest to add hosts entries to your (and your servers)/etc/hosts file.
Set up Tyk Gateway with Quick Start Script
You can set up the core settings for Tyk Gateway with a single setup script, however for more involved deployments, you will want to provide your own configuration file.
You need to replace
<hostname> for --redishost=<hostname>with your own value to run this script.--dashboard=1: We want to use the Dashboard, since Tyk Gateway gets all it’s API Definitions from the Dashboard service, as of v2.3 Tyk will auto-detect the location of the dashboard, we only need to specify that we should use this mode.--listenport=8080: Tyk should listen on port 8080 for API traffic.--redishost=<hostname>: Use Redis on the hostname: localhost.--redisport=6379: Use the default Redis port.
- Set Tyk to listen only on a specific domain for all API traffic.
- Set an API to listen on a specific domain (e.g. api1.com, api2.com).
- Split APIs over a domain using a path (e.g. api.com/api1, api.com/api2, moreapis.com/api1, moreapis.com/api2 etc).
- If you have set a hostname for the Gateway, then all non-domain-bound APIs will be on this hostname + the
listen_path.
Install Tyk on Debian or Ubuntu
Install Database
Using Shell
Requirements Before installing the Tyk components in the order below, you need to first install Redis and MongoDB/SQL. Getting Started- MongoDB
- SQL
Install MongoDB 4.0You should follow the online tutorial for installing MongoDb. We will be using version 4.0. As part of the Mongo installation you need to perform the following:
- Import the public key
- Create a list file
- Reload the package database
- Install the MongoDB packages
- Start MongoDB
- Check the
mongodservice is running
- Dashboard
- Pump
-
Gateway
For a production environment, we recommend that the Gateway, Dashboard and Pump are installed on separate machines. If installing multiple Gateways, you should install each on a separate machine. See Planning for Production For more details.
Using Ansible
Requirements Ansible - required for running the commands below. Use the Shell tab for instructions to install Tyk from a shell. Getting Started- clone the tyk-ansible repositry
cdinto the directory
- Run initialisation script to initialise environment
-
Modify
hosts.ymlfile to update ssh variables to your server(s). You can learn more about the hosts file here - Run ansible-playbook to install the following:
- Redis
- MongoDB or PostgreSQL
- Tyk Dashboard
- Tyk Gateway
- Tyk Pump
-t redis or -t mongodb or -t pgsql However Redis and MongoDB or PostgreSQL are a requirement and need to be installed for the Tyk Pro installation to run.
Supported Distributions
| Distribution | Version | Supported |
|---|---|---|
| Debian | 10 | ✅ |
| Debian | 9 | ✅ |
| Ubuntu | 21 | ✅ |
| Ubuntu | 20 | ✅ |
| Ubuntu | 18 | ✅ |
| Ubuntu | 16 | ✅ |
vars/tyk.yaml
| Variable | Default | Comments |
|---|---|---|
| secrets.APISecret | 352d20ee67be67f6340b4c0605b044b7 | API secret |
| secrets.AdminSecret | 12345 | Admin secret |
| redis.host | Redis server host if different than the hosts url | |
| redis.port | 6379 | Redis server listening port |
| redis.pass | Redis server password | |
| redis.enableCluster | false | Enable if redis is running in cluster mode |
| redis.storage.database | 0 | Redis server database |
| redis.tls | false | Enable if redis connection is secured with SSL |
| mongo.host | MongoDB server host if different than the hosts url | |
| mongo.port | 27017 | MongoDB server listening port |
| mongo.tls | false | Enable if mongo connection is secured with SSL |
| pgsql.host | PGSQL server host if different than the hosts url | |
| pgsql.port | 5432 | PGSQL server listening port |
| pgsql.tls | false | Enable if pgsql connection is secured with SSL |
| dash.license | Dashboard license | |
| dash.service.host | Dashboard server host if different than the hosts url | |
| dash.service.port | 3000 | Dashboard server listening port |
| dash.service.proto | http | Dashboard server protocol |
| dash.service.tls | false | Set to true to enable SSL connections |
| gateway.service.host | Gateway server host if different than the hosts url | |
| gateway.service.port | 8080 | Gateway server listening port |
| gateway.service.proto | http | Gateway server protocol |
| gateway.service.tls | false | Set to true to enable SSL connections |
| gateway.sharding.enabled | false | Set to true to enable filtering (sharding) of APIs |
| gateway.sharding.tags | The tags to use when filtering (sharding) Tyk Gateway nodes. Tags are processed as OR operations. If you include a non-filter tag (e.g. an identifier such as node-id-1, this will become available to your Dashboard analytics) | |
| gateway.rpc.connString | Use this setting to add the URL for your MDCB or load balancer host | |
| gateway.rpc.useSSL | true | Set this option to true to use an SSL RPC connection |
| gateway.rpc.sslInsecureSkipVerify | true | Set this option to true to allow the certificate validation (certificate chain and hostname) to be skipped. This can be useful if you use a self-signed certificate |
| gateway.rpc.rpcKey | Your organization ID to connect to the MDCB installation | |
| gateway.rpc.apiKey | This the API key of a user used to authenticate and authorize the Gateway’s access through MDCB. The user should be a standard Dashboard user with minimal privileges so as to reduce any risk if the user is compromised. The suggested security settings are read for Real-time notifications and the remaining options set to deny | |
| gateway.rpc.groupId | This is the zone that this instance inhabits, e.g. the cluster/data-center the Gateway lives in. The group ID must be the same across all the Gateways of a data-center/cluster which are also sharing the same Redis instance. This ID should also be unique per cluster (otherwise another Gateway cluster can pick up your keyspace events and your cluster will get zero updates). |
vars/redis.yaml
| Variable | Default | Comments |
|---|---|---|
| redis_bind_interface | 0.0.0.0 | Binding address of Redis |
vars/mongodb.yaml
| Variable | Default | Comments |
|---|---|---|
| bind_ip | 0.0.0.0 | Binding address of MongoDB |
| mongodb_version | 4.4 | MongoDB version |
vars/pgsql.yaml
| Variable | Default | Comments |
|---|---|---|
| postgresql_databases[] | [] | Array of DBs to be created |
| postgresql_databases[].name | tyk_analytics | Database name |
| postgresql_users[] | [] | Array of users to be created |
postgresql_users[0].name | default | User name |
postgresql_users[0].password | topsecretpassword | User password |
| postgresql_global_config_options[] | [] | Postgres service config options |
postgresql_global_config_options[1].option | listen_addresses | Listen address binding for the service |
postgresql_global_config_options[1].value | * | Default value to listen to all addresses |
| postgresql_hba_entries[] | [] | Host based authenticaiton list |
postgresql_hba_entries[4].type | host | Entry type |
postgresql_hba_entries[4].database | tyk_analytics | Which database this entry will give access to |
postgresql_hba_entries[4].user | default | What users this gain access from this entry |
postgresql_hba_entries[4].address | 0.0.0.0/0 | What addresses this gain access from this entry |
postgresql_hba_entries[4].auth_method | md5 | What authentication method to to use for the users |
Install Dashboard
Using Shell
Tyk has its own APT repositories hosted by the kind folks at packagecloud.io, which makes it easy, safe and secure to install a trusted distribution of the Tyk Gateway stack. This tutorial has been tested on Ubuntu 16.04 & 18.04 with few if any modifications. We will install the Tyk Dashboard with all dependencies locally. Prerequisites- Have MongoDB/SQL and Redis installed - follow the guide for installing databases on Debian/Ubuntu.
- Ensure port
3000is available. This is used by the Tyk Dashboard to provide the GUI and the Developer Portal.
-a flag in the second Tyk commands - this is important!):
bionic is the code name for Ubuntu 18.04. Please substitute it with your particular ubuntu release, e.g. focal.- Added the Tyk Dashboard repository
- Updated our package list
apt-get to install the Tyk Dashboard without prompting. Wait for the downloads to complete.
When the Tyk Dashboard has finished installing, it will have installed some init scripts, but it will not be running yet. The next step will be to setup each application - thankfully this can be done with three very simple commands.
Verify the origin key (optional)
Debian packages are signed with the repository keys. These keys are verified at the time of fetching the package and is taken care of by the apt infrastructure. These keys are controlled by PackageCloud, our repository provider. For an additional guarantee, it is possible to verify that the package was indeed created by Tyk by verifying the origin certificate that is attached to the package.
First, you have to fetch Tyk’s signing key and import it.
- sign the key with your ultimately trusted key
- trust this key ultimately
/var/cache/apt/archives. Assuming you found the file tyk-gateway-2.9.4_amd64.deb there, you can verify the origin signature.
Configure Tyk Dashboard
Prerequisites for MongoDB You need to ensure the MongoDB and Redis services are running before proceeding.You need to replace
<hostname> for --redishost=<hostname>, and <IP Address> for --mongo=mongodb://<IP Address>/ with your own values to run this script.Make sure to use the actual DNS hostname or the public IP of your instance as the last parameter.
--listenport=3000: Told the Tyk Dashboard (and Portal) to listen on port 3000.--redishost=<hostname>: The Tyk Dashboard should use the local Redis instance.--redisport=6379: The Tyk Dashboard should use the default port.--domain="XXX.XXX.XXX.XXX": Bind the Tyk Dashboard to the IP or DNS hostname of this instance (required).--mongo=mongodb://<IP Address>/tyk_analytics: Use the local MongoDB (should always be the same as the gateway).--tyk_api_hostname=$HOSTNAME: The Tyk Dashboard has no idea what hostname has been given to Tyk, so we need to tell it, in this instance we are just using the local HOSTNAME env variable, but you could set this to the public-hostname/IP of the instance.--tyk_node_hostname=http://localhost: The Tyk Dashboard needs to see a Tyk node in order to create new tokens, so we need to tell it where we can find one, in this case, use the one installed locally.--tyk_node_port=8080: Tell the Tyk Dashboard that the Tyk node it should communicate with is on port 8080.--portal_root=/portal: We want the portal to be shown on/portalof whichever domain we set for the portal.
You need to replace
<hostname> for --redishost=<hostname>, and <Postgres Host Name>, <Port>, <User>, <Password>, <DB> for --connection_string="host=<Postgres Host Name> port=<Port> user=<User> password=<Password> dbname=<DB>" with your own values to run this script.Make sure to use the actual DNS hostname or the public IP of your instance as the last parameter.
--listenport=3000: Told the Tyk Dashboard (and Portal) to listen on port 3000.--redishost=<hostname>: The Tyk Dashboard should use the local Redis instance.--redisport=6379: The Tyk Dashboard should use the default port.--domain="XXX.XXX.XXX.XXX": Bind the dashboard to the IP or DNS hostname of this instance (required).--storage=postgres: Use storage type postgres.--connection_string="host=<Postgres Host Name> port=<Port> user=<User> password=<Password> dbname=<DB>": Use the postgres instance provided in the connection string(should always be the same as the gateway).--tyk_api_hostname=$HOSTNAME: The Tyk Dashboard has no idea what hostname has been given to Tyk, so we need to tell it, in this instance we are just using the local HOSTNAME env variable, but you could set this to the public-hostname/IP of the instance.--tyk_node_hostname=http://localhost: The Tyk Dashboard needs to see a Tyk node in order to create new tokens, so we need to tell it where we can find one, in this case, use the one installed locally.--tyk_node_port=8080: Tell the dashboard that the Tyk node it should communicate with is on port 8080.--portal_root=/portal: We want the portal to be shown on/portalof whichever domain we set for the portal.
/opt/tyk-dashboard/tyk_analytics.conf in the license field.
Step 2: Start the Tyk Dashboard
Start the dashboard service, and ensure it will start automatically on system boot.

- Your Organization Name
- Your Organization Slug
- Your User Email Address
- Your User First and Last Name
- A Password for your User
-
Re-enter your user Password
For a password, we recommend a combination of alphanumeric characters, with both upper and lower case letters.
127.0.0.1:3000, using the username and password created in the Dashboard Setup screen.
Configure your Developer Portal
To set up your Developer Portal follow our Self-Managed tutorial on publishing an API to the Portal Catalog.Using Ansible
Getting Started- clone the tyk-ansible repositry
cdinto the directory
- Run initialisation script to initialise environment
-
Modify
hosts.ymlfile to update ssh variables to your server(s). You can learn more about the hosts file here -
Run ansible-playbook to install
tyk-dashboard
| Distribution | Version | Supported |
|---|---|---|
| Debian | 10 | ✅ |
| Debian | 9 | ✅ |
| Ubuntu | 21 | ✅ |
| Ubuntu | 20 | ✅ |
| Ubuntu | 18 | ✅ |
| Ubuntu | 16 | ✅ |
vars/tyk.yaml
| Variable | Default | Comments |
|---|---|---|
| secrets.APISecret | 352d20ee67be67f6340b4c0605b044b7 | API secret |
| secrets.AdminSecret | 12345 | Admin secret |
| dash.license | Dashboard license | |
| dash.service.host | Dashboard server host if different than the hosts url | |
| dash.service.port | 3000 | Dashboard server listening port |
| dash.service.proto | http | Dashboard server protocol |
| dash.service.tls | false | Set to true to enable SSL connections |
Install Pump
Using Shell
This tutorial has been tested Ubuntu 16.04 & 18.04 with few if any modifications. Prerequisites- You have installed Redis and either MongoDB or SQL.
- You have installed the Tyk Dashboard.
-a flag in the second Tyk commands - this is important!):
bionic is the code name for Ubuntu 18.04. Please substitute it with your particular ubuntu release, e.g. focal.- Added the Tyk Pump repository
- Updated our package list
apt-get to install Tyk Pump without prompting. Wait for the downloads to complete.
When Tyk Pump has finished installing, it will have installed some init scripts, but it will not be running yet. The next step will be to setup each application using three very simple commands.
Verify the origin key (optional)
Debian packages are signed with the repository keys. These keys are verified at the time of fetching the package and is taken care of by the apt infrastructure. These keys are controlled by PackageCloud, our repository provider. For an additional guarantee, it is possible to verify that the package was indeed created by Tyk by verifying the origin certificate that is attached to the package.
First, you have to fetch Tyk’s signing key and import it.
- sign the key with your ultimately trusted key
- trust this key ultimately
/var/cache/apt/archives. Assuming you found the file tyk-gateway-2.9.3_amd64.deb there, you can verify the origin signature.
You need to replace
<hostname> for --redishost=<hostname>, and <IP Address> for --mongo=mongodb://<IP Address>/ with your own values to run this script.You need to replace
<hostname> for --redishost=<hostname>, and <Postgres Host Name>,<Port>, <User>, <Password>, <DB> for --postgres="host=<Postgres Host Name> port=<Port> user=<User> password=<Password> dbname=<DB>" with your own values to run this script.Using Ansible
Install Tyk Pump Through Ansible Getting Started- clone the tyk-ansible repositry
cdinto the directory
- Run initialisation script to initialise environment
-
Modify
hosts.ymlfile to update ssh variables to your server(s). You can learn more about the hosts file here -
Run ansible-playbook to install
tyk-pump
| Distribution | Version | Supported |
|---|---|---|
| Debian | 10 | ✅ |
| Debian | 9 | ✅ |
| Ubuntu | 21 | ✅ |
| Ubuntu | 20 | ✅ |
| Ubuntu | 18 | ✅ |
| Ubuntu | 16 | ✅ |
Install Gateway
Using Shell
Tyk has it’s own APT repositories hosted by the kind folks at packagecloud.io, which makes it easy, safe and secure to install a trusted distribution of the Tyk Gateway stack. This tutorial has been tested on Ubuntu 16.04 & 18.04 with few if any modifications. Please note however, that should you wish to write your own plugins in Python, we currently have a Python version dependency of 3.4. Python-3.4 ships with Ubuntu 14.04, however you may need to explicitly install it on newer Ubuntu Operating System releases. Prerequisites- Ensure port
8080is available. This is used in this guide for Gateway traffic (API traffic to be proxied). - You have MongoDB and Redis installed.
- You have installed firstly the Tyk Dashboard, then the Tyk Pump.
/etc/apt/sources.list.d/tyk_tyk-gateway.list with the following contents:
bionic is the code name for Ubuntu 18.04. Please substitute it with your particular ubuntu release, e.g. focal.- Added the Tyk Gateway repository
- Updated our package list
apt infrastructure. These keys are controlled by PackageCloud, our repository provider. For an additional guarantee, it is possible to verify that the package was indeed created by Tyk by verifying the origin certificate that is attached to the package.
First, you have to fetch Tyk’s signing key and import it.
- sign the key with your ultimately trusted key
- trust this key ultimately
/var/cache/apt/archives. Assuming you found the file tyk-gateway-2.9.4_amd64.deb there, you can verify the origin signature.
/etc/hosts file.
Set up Tyk
You can set up the core settings for Tyk Gateway with a single setup script, however for more involved deployments, you will want to provide your own configuration file.
You need to replace
<hostname> for --redishost=<hostname>with your own value to run this script.--dashboard=1: We want to use the Dashboard, since Tyk Gateway gets all it’s API Definitions from the Dashboard service, as of v2.3 Tyk will auto-detect the location of the dashboard, we only need to specify that we should use this mode.--listenport=8080: Tyk should listen on port 8080 for API traffic.--redishost=<hostname>: Use Redis on your hostname.--redisport=6379: Use the default Redis port.
- Set Tyk to listen only on a specific domain for all API traffic.
- Set an API to listen on a specific domain (e.g. api1.com, api2.com).
- Split APIs over a domain using a path (e.g. api.com/api1, api.com/api2, moreapis.com/api1, moreapis.com/api2 etc).
- If you have set a hostname for the Gateway, then all non-domain-bound APIs will be on this hostname + the
listen_path.
Using Ansible
Getting Started- clone the tyk-ansible repositry
cdinto the directory
- Run initialisation script to initialise environment
-
Modify
hosts.ymlfile to update ssh variables to your server(s). You can learn more about the hosts file here -
Run ansible-playbook to install
tyk-gateway
| Distribution | Version | Supported |
|---|---|---|
| Debian | 10 | ✅ |
| Debian | 9 | ✅ |
| Ubuntu | 21 | ✅ |
| Ubuntu | 20 | ✅ |
| Ubuntu | 18 | ✅ |
| Ubuntu | 16 | ✅ |
vars/tyk.yaml
| Variable | Default | Comments |
|---|---|---|
| secrets.APISecret | 352d20ee67be67f6340b4c0605b044b7 | API secret |
| secrets.AdminSecret | 12345 | Admin secret |
| gateway.service.host | Gateway server host if different than the hosts url | |
| gateway.service.port | 8080 | Gateway server listening port |
| gateway.service.proto | http | Gateway server protocol |
| gateway.service.tls | false | Set to true to enable SSL connections |
| gateway.sharding.enabled | false | Set to true to enable filtering (sharding) of APIs |
| gateway.sharding.tags | The tags to use when filtering (sharding) Tyk Gateway nodes. Tags are processed as OR operations. If you include a non-filter tag (e.g. an identifier such as node-id-1, this will become available to your Dashboard analytics) | |
| gateway.rpc.connString | Use this setting to add the URL for your MDCB or load balancer host | |
| gateway.rpc.useSSL | true | Set this option to true to use an SSL RPC connection |
| gateway.rpc.sslInsecureSkipVerify | true | Set this option to true to allow the certificate validation (certificate chain and hostname) to be skipped. This can be useful if you use a self-signed certificate |
| gateway.rpc.rpcKey | Your organization ID to connect to the MDCB installation | |
| gateway.rpc.apiKey | This the API key of a user used to authenticate and authorize the Gateway’s access through MDCB. The user should be a standard Dashboard user with minimal privileges so as to reduce any risk if the user is compromised. The suggested security settings are read for Real-time notifications and the remaining options set to deny | |
| gateway.rpc.groupId | This is the zone that this instance inhabits, e.g. the cluster/data-center the Gateway lives in. The group ID must be the same across all the Gateways of a data-center/cluster which are also sharing the same Redis instance. This ID should also be unique per cluster (otherwise another Gateway cluster can pick up your keyspace events and your cluster will get zero updates). |